Today, let’s pivot from hacking into the mysterious realm of containers. Containers are the backbone of today’s infrastructure, providing lightweight environments for running applications. Docker might ring a bell, but ever wondered about the magic behind the scenes? Let’s delve deep by building our container using Go, a popular programming language known for its simplicity…More
Category Archives: Uncategorized
Introducing Commander: A Command and Control Framework for Security Testing
Are you looking for a versatile and powerful command and control (C2) framework for your security testing needs? Look no further! Introducing Commander, a C2 framework written in Python, Flask, and SQLite, featuring two agents in Python and C. Commander is designed for seasoned security professionals and is not script-kiddie friendly. Its key features include:…More
Introducing Paraforce: A Powerful and Configurable SSH Brute Force Tool
Say goodbye to weak SSH passwords with Paraforce, a highly customizable Python-based brute force solution. Find the source code on GitHub As cybersecurity threats continue to evolve, it’s essential to stay one step ahead. Brute force attacks remain a prevalent threat, and SSH logins are no exception. To help combat this, I introduce Paraforce, a…More
HTB – Grandpa/Granny Walk-through
Today we will root two boxes from HTB that are so similar that the same techniques can be used. The boxes are the Grandpa and Granny. Also we will escalate our privilages with two different manual ways Initial foothold PrivEsc with Churrasco PrivEsc with MS14-070 As always we start the scan with nmap We see…More
HTB – Jerry Walk-through
Today we will root manually the Devel Box. Let’s see how We scan the machine The only service that this machine has is an Apache Tomcat service. If we visit the ip on that port we do not see anything useful. As we know that this is a tomcat server we can visit the /manager…More
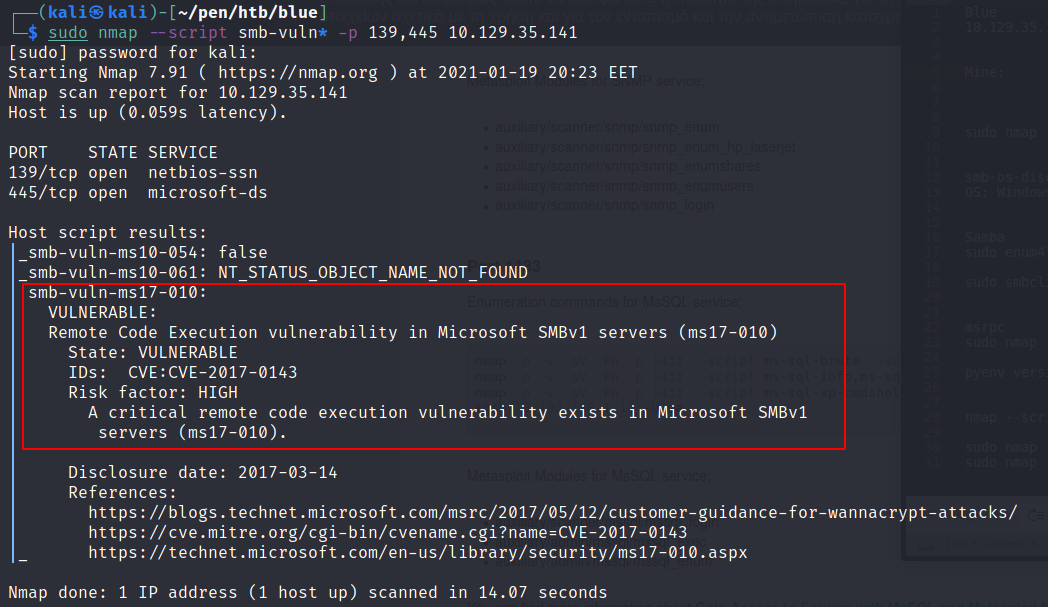
HTB – Blue Walk-through
Today we will root with metasploit and manually the Blue Box. Let’s see how First we do our usual scan We see multiple ports open but the most interesting is the smb service. Before we enumerate smb we check also the msrpc service with the nmap script engine. But there is nothing interest from the…More
HTB – Lame Walk-through
Today we will see how to root the Lame box, so let’s start We start with the usual port scanning The most interesting ports are the smb service (139,445) and the ftp (21). At first we see that the version of smb is 3.0.20-Debian and is a linux box. We also see that the ftp…More
HTB – Legacy Walk-through
This is my first walk-through for a very old machine from Hack The Box page. Also this is my first box 🙂 We will see how we can root it both with metasploit and manually. At the time this blog post was written, Python 2 has reached EOL and is no longer being maintained in…More
SLAE32 – Assignment #7 – Create a Custom Crypter
This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certificationhttp://securitytube-training.com/onlinecourses/securitytube-linux-assembly-expert/Student ID: PA-27669 The code and scripts for this assignment can be found on github The goal of this assignment Create a custom crypter like the one shown in the “crypters” video Free to use any existing encryption schema Can…More
SLAE32 – Assignment #6 – Generate polymorphic shellcodes
This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certificationhttp://securitytube-training.com/onlinecourses/securitytube-linux-assembly-expert/Student ID: PA-27669 The code and scripts for this assignment can be found on github The goal of this assignment Take up three shellcodes from Shell-Storm and create polymorphic versions of them to beat pattern matching The polymorphic versions cannot…More